All Courses
Risk Manager enables you to quickly evaluate your organization's security posture and connect with insurance partners to obtain specialized cyber cover for GCP.
Compliance frameworks were designed for traditional data centers and not for the cloud. It’s easier to lift and shift, but that doesn’t work for Kubernetes. The security risk per component reduces with Kubernetes. However, meeting regulatory and compliance requirements are still the top concerns due to increased infrastructure velocity and complicated threat vectors. In this talk we uncover how to cross these hurdles and make compliance business as usual on GKE. We will cover how to meet compliance requirements for networking, segmentation, access control, and data protection on GKE. Armed with this information, we will discuss how to present this to your auditor.
It’s the responsibility of the manager or supervisor to ensure that employees are being trained properly.
In one of my popular articles and videos The Seven Steps for Training and Coaching Employees, I explained the seven-step process to dramatically improve the effectiveness of employee training and, ultimately, the performance of employees.

Your weekly team meeting is an opportunity to celebrate any wins from the last week, which can feel incredibly reenergizing for the whole team!
Matterhorn Business Development

The NIST HIPAA Security Toolkit Application, developed by the National Institute of Standards and Technology (NIST), is intended to help organizations better understand the requirements of the HIPAA Security Rule, implement those requirements, and assess those implementations in their operational environment.

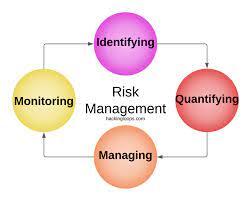
The Award-winning FAIR Book provides a practical and credible model for understanding, measuring, and analyzing information risk of any size and complexity. It shows how to deliver financially derived results tailored for enterprise risk management. It is intended for organizations that need to build a risk management program.